Kelly W Shelton
Park University – Goodfellow AFB
The purpose of this report is to detail the various layers of the International Standards Organization Open Systems Interconnect (OSI) model, one of several network modeling standards currently in use. It is intended that readers of this document will develop an understanding of the OSI model’s function and a general working knowledge of the role each layer plays in the development of networks and data communication. This document is based primarily on a number of published works that interpret the source documentation specifying the OSI model in support of their specific internetworking subject matter.
Open Systems Interconnection Reference Model
The Open Systems Interconnection (OSI) reference model describes how information generated by an application in one computer is transmitted through a network to an application in another computer. This model was initially developed by the International Organization for Standardization (ISO) in 1984, and in its present form, ISO/IEC 7498-1 Information Technology - Open Systems Interconnection - Basic Reference Model: The Basic Model (2nd ed., 1994), is now considered the primary architectural model for inter-computer communications.
The OSI reference model is a seven layer conceptual structure (see Figure 1), with each layer specifying particular network functions. Each of the model layers is self-contained, so that the tasks assigned to each layer can be implemented independently, enabling the solutions offered by one layer to be updated with minimal impact on the adjacent layers.
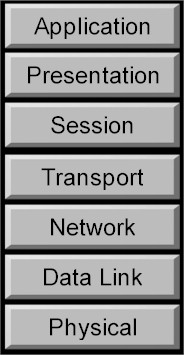
The seven layers of the OSI reference model can be divided into two categories: upper and lower layers.
The three upper layers of the OSI model (application, presentation and session) provide end user service and, generally speaking, are application oriented, applying only to software. The highest layer, application, resides closest to the end user. Both users and application-layer processes interact with software that contains communication components.
The lower four layers of the OSI model (transport, network, data link and physical) handle data transport issues and are communication oriented. The physical layer and data-link layer are implemented in both hardware and software. The remaining layers are implemented only in software. The lowest layer, the physical layer, is closest to the physical hardware that allows data transfer across the network.
The OSI Model and Intersystem Communication
While the OSI model provides a conceptual framework for communication between computers, the model itself is not a method of communication. Actual communication is made possible by using formal rules and conventions called protocols. A protocol implements the functions of one or more of the OSI layers and governs how computers exchange information over a network medium. A wide variety of communication protocols exist, however, all fall into one of the following groups: Local Area Network (LAN), Wide Are Network (WAN) and/or routing protocols. A LAN protocol operates at the physical and data-link layers of the OSI model and defines communication over various LAN media. WAN protocols operate at the lowest three layers of the OSI model and define communication over the various wide-area media. Routing protocols are responsible for path determination and traffic switching and operate primarily in the network layer.
Information being transferred from a software application in one computer system to a software application in another must pass through each of the OSI layers.
A given layer will usually communicate with three other OSI layers: the layer directly above it, the layer directly below it, and its peer layer in another networked computer system. One OSI layer communicates with the next layer to make use of the services provided by the second layer. The services provided by an adjacent layer assists a given OSI layer to communicate with its peer layer in other computer systems (see Figure 2).
Figure 2, Actual and Peer-to-Peer Communication
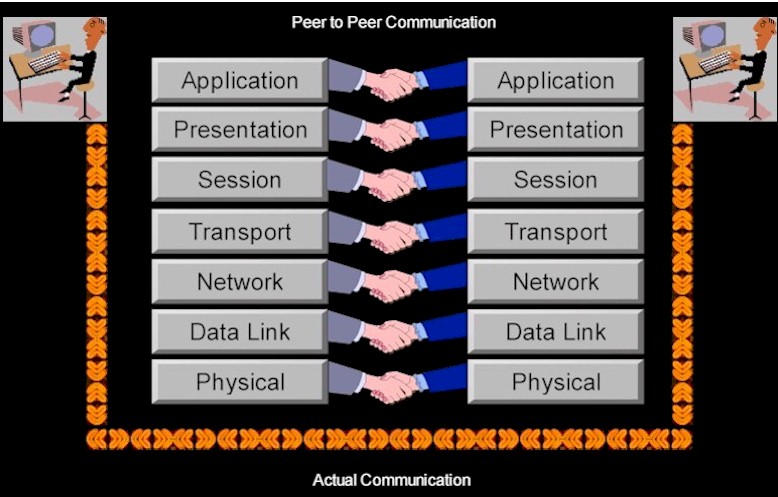
The OSI layers use various forms of control information to communicate with their peer layers in other computer systems. As each layer in the source system adds control information to data, the corresponding layer in the destination system will analyze and remove the control information from that data upon receipt.
The application layer is the OSI layer closest to the end user. Both the OSI application layer and the user interact directly with the software application that implements communication. Application-layer functions typically include identifying communication partners, determining resource availability, and synchronizing communication.
When identifying communication partners, the application layer determines the identity and availability of communication partners for an application with data to transmit. When determining resource availability, the application layer must decide whether sufficient network resources for the requested communication exist. In synchronizing communication, all communication between applications requires cooperation managed by the application layer.
Two key types of application-layer implementations are TCP/IP applications and OSI applications. TCP/IP applications are protocols, such as Telnet, used for remote login, File Transfer Protocol (FTP), for transmitting files between computers on the Internet, and Simple Mail Transfer Protocol (SMTP), used to transfer electronic mail between computers, usually over Ethernet, all of which exist in the Internet Protocol suite. OSI applications are protocols, such as File Transfer, Access, and Management (FTAM), an application layer protocol for file transfer and remote manipulation existing in the OSI suite.
The presentation layer provides coding and conversion functions that are applied to application layer data. These functions ensure information that is sent from the application layer of one system, is readable by the application layer of a receiving system. Some examples of presentation layer coding and conversion schemes include; common data representation formats, conversion of character representation formats, common data compression schemes for encoding information while reducing the bandwidth or bits required for transmission, and common data encryption schemes for information security.
The session layer establishes, manages, and terminates communication sessions between presentation layer entities.
Communication sessions consist of requests and responses, commonly called session services, that occur between applications located in different network devices and are coordinated by protocols implemented at the session layer. Some examples of session-layer implementations include Zone Information Protocol (ZIP), that maintains mappings of zone names to network numbers on internet routers and Session Control Protocol (SCP), which lets a server and client have multiple conversations over a single TCP connection.
The transport layer implements reliable inter-network data transport services that are transparent to upper layers.
Transport-layer functions typically include flow control, multiplexing, virtual circuit management, and error checking and recovery. Flow control manages data transmission between devices so that the transmitting device does not send more data than the receiving device can process. Multiplexing enables data from several applications to be transmitted onto a single physical link. Virtual circuits are established, maintained, and terminated by the transport layer. Error checking involves creating various mechanisms for detecting transmission errors, while error recovery involves taking an action, such as requesting that data be retransmitted, to resolve any errors that occur.
Some transport-layer implementations include Transmission Control Protocol, Name Binding Protocol, and OSI transport protocols. Transmission Control Protocol (TCP) is the protocol in the TCP/IP suite that provides reliable transmission of data. Name Binding Protocol (NBP) is the protocol that associates AppleTalk names with addresses. OSI transport protocols are a series of transport protocols in the OSI protocol suite.
The network layer provides routing and related functions that enable multiple data links to be combined into an inter-network through logical addressing of devices. The network layer supports both connection-oriented and connectionless service from higher-layer protocols. Network-layer protocols typically are routing protocols, but other types of protocols are implemented at the network layer as well. Some common routing protocols include Border Gateway Protocol (BGP), for inter-autonomous system routing,. and Routing Information Protocol (RIP) used for routing traffic in the global Internet performing routing within a single autonomous system.
Two well-known specifications of this layer are X.25, developed to describe how data passes into and out of public data communications networks, and Integrated Services Digital Network (ISDN), a set of communications standards allowing a single wire or optical fiber to carry voice, digital network services and video.The data link layer provides transport of data across a physical network link. Different data link layer specifications define different network and protocol characteristics, including physical addressing, network topology, error notification, sequencing of frames, and flow control. Physical addressing defines how devices are addressed at the data link layer, using identifiers such as the Media Access Control (MAC) address to ensure packets are sent to the correct machine on the network. Network topology consists of the data-link layer specifications that often define how devices are to be physically connected. Error notification alerts upper-layer protocols that a transmission error has occurred while flow control moderates the transmission of data so that the receiving device is not overwhelmed with more traffic than it can handle at a given time. Protocols for this layer include IEEE 802.3, defining the hardware and transport layer of (a variant of) Ethernet, and IEEE 802.5, which defines the token ring standard.
As bottom-most layer of the OSI model, the physical layer defines the specifications of hardware (electrical and mechanical), procedures, and functions for activating, maintaining, and deactivating the physical link between communicating network systems. It manifests as the component that resides between the host and the media. Network characteristics covered by this layer include maximum transmission distances, voltage levels, data rates, and physical connectors. Physical-layer implementations are categorized as either LAN or WAN specifications. ISO recommended interfaces for this layer include X.21, a type of digital signaling interface, and RS-232-C, defining interchange circuits between Data Terminal Equipment(DTE) and Data Communication Equipment (DCE).
The advantages of client/server systems are often lost through poor planning and budgeting. Companies will squander vast amounts of resources through elaborate integration and reengineering schemes without a solid methodology for network technology implementation. The Open Systems Interconnection Reference Model provides a definitive guideline for developing those methodologies required to properly plan and implement an open client/server system.
Baccala, B. (1997, April) OSI seven-layer model. Connected: An Internet Encyclopedia. [On-line]. Available: <http://cie.bilkent.edu.tr/Topics/15.htm> [2000, Sept. 21]
Chapin, A.L. & Piscitello, D. (1993) Open systems networking : TCP/IP and OSI (pp. 40-44). Boston, MA: Addison-Wesley Professional Computing
Cisco Systems Inc. (1998). Internetworking technologies handbook. [On-line]. Available: <http://www.cisco.com/cpress/cc/td/cpress/fund/ith/ith01gb.htm> [2000, Sept. 21].
Doyle, P. & Engst, A.C. (September 1995). Upgrading & repairing networks (pp.415-416). Indianapolis, IN: Que
Ferrell, J. (1997). A guide to networking for K-12 schools. [Appendix C]. Northwest Educational Technology Consortium. [On-line]. Available: <http://www.netc.org/network_guide/c.html> [2000, Sept. 21]
Howe, D. (1993) ] Open systems interconnect. [Definition] The Free On-line Dictionary of Computing. [On-line] Available: <http://www.wkonline.com> [2000, Sept. 7]
International Organization for Standardization. (1994). ISO/IEC 7498-1 Information technology - open systems interconnection - basic reference model: the basic model (2nd ed.). Geneva, Switzerland: Author.
Taylor, D.E. (September 1997). McGraw-Hill internetworking handbook, 2nd ed. (pp.373-405). New York: The McGraw-Hill Companies
Vargo, J., & Hunt, R. (1996). Telecommunications in business: strategy and application (pp.152-154, 211). New York: The McGraw-Hill Companies