U.S. Military and SQL Slammer Smoking Guns
Exhibit B: Net Census data analysis reveals amazing details
Feb. 7, 2003By Doctor Electron
In late January, Net Census reported the major role of the U.S. military in the recent SQL Slammer worm attack on the internet in an exclusive story. Data gathered in our internet research was analyzed to show that the U.S. military played three key roles in this internet crisis -- as victim, as a potent agent propagating the worm and finally as helper in controlling the internet traffic jam.
Now the smoking gun has been found (Table 1). With this evidence, little doubt remains that the participation of the U.S. military and its inadvisable internet practices largely explain the extremely rapid worm spread which mystified experts.
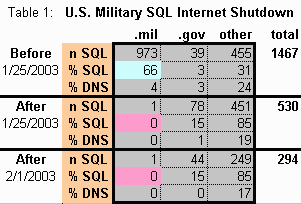
Legend: Three periods before and after the SLQ Slammer worm attack (rows). Columns tabulate U.S. military (.mil), U.S. government (.gov), and other (all other computers in all countries connected to the internet). n SQL, number of internet addresses connecting on SQL tcp port 1433 (or udp port 1434). % SQL, percent of worldwide totals. % DNS, percent of SQL internet addresses with available host names. About 1.8 million randomly selected internet addresses were tested to obtain this sample. Sample sizes (right column) could be used to calculate confidence intervals for the percents.The smoking gun is that U.S. military sites accounted for two-thirds (66%) of all SQL internet addresses worldwide before the worm attack. Who would have thought? This evidence of "internet address funneling" for this particular internet service -- SQL -- is almost beyond belief.
Furthermore, a rather small fraction of all U.S. military networks are responsible for this risky internet practice, according to the Net Census database.
This smoking gun suggests that some military internet managers may also be smoking something that is proscribed. Are we expected to believe that two out of every three computers in the world is in less than one half of U.S. military installations? That all other computers -- all the rest of the U.S. military, all countries, all governments, all universities, all corporations, all other organizations and networks, everybody else -- are only half as many as the total that a fraction of the U.S. military has?
In actual fact, these particular U.S. military locations probably have roughly the same number of computers as other computerized organizations, whether military or not. Thus, their practice of internet address funneling is clearly exposed.
Item: U.S. military internet address funneling.
Status: conviction obtained; case closed; many questions remain.
Juror comment: "It is like they tried to be a target."The evidence also shows that this insecure funneling practice was most probably a planned program rather than isolated misconfigurations of internet interface equipment.
In fact, an "operation funnel" was launched at identified locations in all major branches of our armed forces including army, navy, air force and marine corps. No doubt, there was a code name for this operation, perhaps intended to gather intelligence or act as some sort of crude honeypot.
Such a major undertaking would require an entity to plan and implement it. Who? A military contractor? What risk analysis was done? Did the operation commander know anything about propagation methods used by computer worms and virii? In this context, "operation funnel" was destined to become "operation fumble".
"Don't worry, son, just tell the truth and learn from your mistakes." The original Net Census report concluded that the U.S. military probably was the major agent propagating the SQL Slammer worm causing a breakdown in internet communications. Given the 66% cited above, we can delete the word "probably" in this conclusion and explain why the worm spread was so rapid.
The 66% SQL vulnerability of certain U.S. military networks mixed with the penchant for rapid fire of the attack ammunition -- udp packets -- was a near perfect match of scanning ammo with funneling victim.
Did the perpetrators know these facts beforehand? That U.S. military systems were most vulnerable and most likely to become the major propagation agent of this guerilla warfare type attack? Was the game plan "Don't fight Goliath; make Goliath do the fighting for you"?
Item: U.S. military as foremost SQL worm propagation agent.
Status: conviction obtained; case closed; many questions remain.
Juror comment: "They didn't wear gloves. 66%. They left fingerprints everywhere."What happened next? In January, Net Census reported that the worm crisis was managed by shutting down computers on a massive scale and that most of this shutdown was done by the U.S. military.
These conclusions were based on marked trends previously reported by Net Census about the internet behavior of the U.S. military. The present focus on just one network service -- SQL -- shows that our previous data and analysis could not have been more correct.
In short, the gigantic SQL presence of the U.S. military has essentially vanished (pink in Table 1). The single SQL internet address in our data sample that remains is not even enough to rate above zero percent. Somebody used a meat axe. Imagine the stories behind the scenes at U.S. military computer centers over that fateful SQL Slammer weekend.
A second smoking gun. Now there is a gun for each hand of the U.S. military computer networks, making "66%" and "0%" smoke rings. It seems that the SQL Slammer has caused a permanent change in the landscape.
"Please stand back and do not cross the yellow 'crime scene' ribbon.
The bodies have already been removed from the scene."Do your Congressmen and Senators know yet about the "massacre" that happened here?
Where were "the bodies" taken? Maybe some went to the proverbial morgue. But note that before the worm attack, U.S government computer networks accounted for about 8% of all "other" SQL internet services [100 x 39 / (39 + 455) = 7.9%] (Table 1). After the attack to the present writing, U.S. government SQL internet services jump to 15% of similar activity worldwide, almost doubling the internet presence before the attack.
Our observations suggest that some of this increase may come thanks to our friends at sandia.gov.
In any case, were vital SQL database services shifted from .mil to .gov domains? If so, why would such a move of SQL databases from .mil to .gov sites be done? What security issues are involved? Is this a scotch-tape fix which may be as risky as the questionable military internet practices that clearly occupied center stage in this internet crisis?
Check with your elected representatives about the security of the nation's civil, governmental and military computer networks. Maybe they can get answers.
This stunning SQL shutdown could be done in several ways. For example, SQL connection or udp requests from unknown internet computers may simply be blocked. Or the SQL services may be disabled for all users, including military personnel.
Item: Shutdown SQL computer internet connections mostly by U.S. military.
Status: conviction obtained; case closed; many questions remain.
Juror comment: "Who else could go from 66% to 0%?"Meanwhile, Net Census data collection indicates a wide range of organizations, both in the U.S. and abroad, operate SQL database services and continue to do so after the worm attack. These include many countries around the world as well as diverse academic and commercial organizations. Was their computer security better than that of certain U.S. military neworks?
And let us not forget the general internet address funneling first reported by Net Census for all of the other service categories. Do these represent more disasters waiting to happen? Stay tuned to Net Census for more exclusive stories on this front.
The "right someones" should ask the "right someone elses" and get some answers to these questions in this front-page story. When are the Senate hearings on the U.S. military role in this extraordinary SQL Slammer assault on the worldwide internet?
"I am sorry, sir. Answers to your questions are classified information." If the good guys can collect and analyze this type of information, so can the bad guys. This central point is featured in many Net Census research reports. Thus, by definition, this is not classified information insofar as it is publicly available. Indeed, it is provided by internet authorities known as registries and by the military networks themselves as our reports indicate.
If network operators do not want to freely hand out detailed information about their activities because it is viewed as "classified", their networks should be configured accordingly.
Notes:
This story is rapidly developing and more details will be added to this breaking Net Census news exclusive on the U.S. military and its computer security at a time when war looms and when internet communications may be an essential asset in these events.The "unit" for a network in the SQL reports described as having "over 64,000" internet addresses each is known as a x.y/16 CIDR address prefix. The .mil and other categories were determined from public information provided by the ARIN and other internet registries. Perhaps it is ironic that military computers without DNS entries for reverse DNS lookup are listed as .mil by ARIN, so there is no "secret".
Statistics presented refer to the subset of our database obtained with methods previously published by Net Census. In this subset, almost 11,000 x.y/16 address blocks of the over 64,000 possible, have shown responses to our tests. But only about 29% of interent addresses can be routed over the internet. This gives us around 19,000 "real" x.y/16 networks where some computers might be online. Thus, our samples document internet behavior of over half of these.
However, just because a packet destined for an internet address is routable does not mean that host computers are online to receive it or that firewalls will allow its delivery. Thus, the some 11,000 address blocks in our present database probably represent most of the "online" computer hosts in the world, subject to qualifications described.
It is important to note that many .mil address blocks have shown no responses to those particular methods and are not in the sample considered. This means that the U.S. military x.y/16 address blocks contributing to the SQL and other results described are even a smaller minority of all such .mil networks than might be assumed from the descriptions presented. Perhaps those figures could also be tabulated for an improved perspective. In brief, however, this consideration further emphasizes the noteworthy effects of this minority of military networks.
About the author:
The author is a U.S. citizen who supports efforts to improve the security of the internet, the United States, the U.S. military and the brave men and women who serve in the U.S. military.Copyright © 2003 Global Services
Original publication: Feb. 7, 2003Back to Net Census