Internet Explorer Cannot Read Microsoft Web Site
by Doctor Electron and Maj. Hog
Using Internet Explorer 5.5, the following error seems to occur on virtually all pages at Microsoft Corporation's web site:
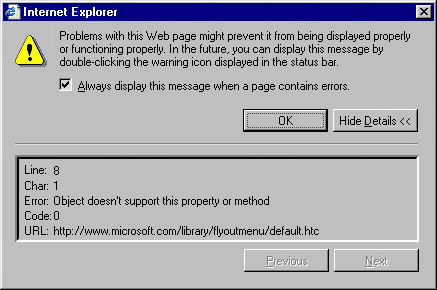
By the way, Internet Explorer is a Microsoft program. So we have the largest and perhaps greatest software company in the world producing a web browser that cannot read the web site of the company itself without error. Naturally, I have all scripting of any kind turned off. But this more secure configuration of Internet Explorer cannot be considered as unusual, since Microsoft itself publicly recognizes the need for improved security measures in internet activity.
How can it be, then, that the home page of Microsoft seems to expect that browsers such as it's own Internet Explorer would be configured insecurely? Why does this home page not detect such insecure configurations and advise visitors to immediately disable all scripting in their browsers? The popup window, if any, might better say, "Your browser has scripting enabled. Please disable scripting for improved security of your computer." Of course, it should be obvious that Microsoft might be the leader in showing how to write non-intrusive web pages which are free of all scripting.
Even though scripting is disabled, the script files are downloaded to the computer of the visitor of the Microsoft web site anyway, wasting internet bandwidth and the computer resources and money of the visitor. The "default.htc" file shown in the graphic above is 16,000 bytes. Another called "deeptree.htc", 30,000 bytes, was sent by another Microsoft page. These files were retrieved from the Temporary Internet Files directory and consist of lengthy JScript (java script) programs.
Net Census is a family site, so we will not risk offending our readers with a detailed description of the contents of these script programs that Micosoft wants to run on the computer of the visitor. However, they clearly do provide a good illustration of the intrusive techniques described elsewhere [e.g.,Webhogs FAQ]. The general strategy is invade and occupy, stopping function of the visitor's programs, if necessary, by swapping them out of RAM to the hard drive. In case you are wondering, none of this hogging of your computer resources is necessary to look up information on a web site. Indeed, it is not easy to explain why otherwise reputable web site operators would impose on visitors these kinds of abuses. One might think that it would be more advisable for web sites to roll out the welcome mat.
For the reader who is new to the idea that web sites can send their programs to run on his or her computer when a web site is visited, here is one way to look at it. It is similar to what malicious hackers do -- get their programs running on your computer. If the script programs from a web site become corrupted for whatever reason, the visitor's computer can also be corrupted. In this light, web sites that engage in this practice are essentially saying, "Our problems will be your problems." The visitor to the web site might rather say, "I don't want your problems. If you have a problem with an employee or whatever, keep it to yourself. I don't need to know, especially by having your web site send me a program that might reformat my hard drive."
In brief, "Dear Microsoft: We hear you talk about improving security. Now show us you can improve security by producing script-free home pages. As long as we see the popup window shown above, we know it's still just talk, not action. We have noticed that you produce and sell a web page design product. Show us you know how to write a web page. We have seen pictures of your building. There must be someone in there who knows how to write a web page. Thank you."
Postscript: This little commentary is not part of any anti-Microsoft effort. To the contrary, Microsoft should be applauded for its many significant achievements which have contributed to society.
Copyright © 2002 Global Services
Original Publication: October 26, 2002
Back to Net Census