LoveLetter Virus will once again activate and may cause damage to many computers. At this point MIS can only hope that our email users have update to an up-to-date Antivirus Dat file to 4078.
In conjunction with other anti-virus vendors, it has renamed this worm from VBS.LoveLetter.FW.A to VBS.NewLove.A.
The VBS.NewLove.A is a worm, and spreads by sending itself to all addressees in the Outlook address book when it is activated.
The attachment name is randomly chosen, but will always have a .Vbs extension. The subject header will begin with "FW: " and will include the name of the randomly chosen attachment (excluding the .VBS extension) Upon each infection, the worm introduces up to 10 new lines of randomly generated comments in order to prevent detection.
Also known as
VBS/Loveletter.ed, VBS/Loveletter.Gen, VBS_SPAMMER, VBS.Loveletter.FW.APlease make sure your virus .dat files(4078) are current.
And also
please exercise extreme caution when handling any arrival email andDO NOT open any attachments with extension .vbs
.VBS.LoveLetter.A
Norton AntiVirus detects as: VBS.LoveLetter.A(1)
ATTACHMENT: LOVE-LETTER-FOR-YOU.TXT.vbs
SUBJECT LINE: ILOVEYOU
MESSAGE BODY: kindly check the attached LOVELETTER coming from me.
VBS.LoveLetter.B (also known as Lithuania)
Norton AntiVirus detects as: VBS.LoveLetter.B(1)
ATTACHMENT: same as A
SUBJECT LINE: Susitikim shi vakara kavos puodukui...
MESSAGE BODY: same as A
VBS.LoveLetter.C (also known as Very Funny)
Norton AntiVirus detects as: VBS.LoveLetter.C(1)
ATTACHMENT: Very Funny.vbs
SUBJECT LINE: fwd: Joke
MESSAGE BODY: empty
VBS.LoveLetter.D (also known as BugFix)
Norton AntiVirus detects as: VBS.LoveLetter.A(1)
ATTACHMENT: same as A
SUBJECT LINE: same as A
MESSAGE BODY: same as A
MISC. NOTES: registry entry: WIN- -BUGSFIX.exe instead of WIN-BUGSFIX.exe
VBS.LoveLetter.E (also known as Mother's Day)
Norton AntiVirus detects as: VBS.LoveLetter.E
ATTACHMENT: mothersday.vbs
SUBJECT LINE: Mothers Day Order Confirmation
MESSAGE BODY: We have proceeded to charge your credit card for the amount of $326.92 for the mothers day diamond special. We have attached a detailed invoice to this email. Please print out the attachment and keep it in a safe place.Thanks Again and Have a Happy Mothers Day! mothersday@subdimension.com
MISC. NOTES: mothersday.HTM sent in IRC, & comment: rem hackers.com, & start up page to hackes.com, l0pht.com, or 2600.com
VBS.LoveLetter.F (also known as Virus Warning)
Norton AntiVirus detects as: VBS.LoveLetter.F
ATTACHMENT: virus_warning.jpg.vbs
SUBJECT LINE: Dangerous Virus Warning
MESSAGE BODY: There is a dangerous virus circulating. Please click attached picture to view it and learn to avoid it.
MISC. NOTES: Urgent_virus_warning.htm
VBS.LoveLetter.G (also known as Virus ALERT!!!)
Norton AntiVirus detects as: VBS.LoveLetter.Variant or VBS.LoveLetter.G
ATTACHMENT: protect.vbs
SUBJECT LINE: Virus ALERT!!!
MESSAGE BODY: a long message regarding VBS.LoveLetter.A
MISC. NOTES: FROM support@symantec.com. This variant also overwrites files with .bat and .com extensions.
VBS.LoveLetter.H (also known as No Comments)
Norton AntiVirus detects as: VBS.LoveLetter.A
ATTACHMENT: same as A
SUBJECT LINE: same as A
MESSAGE BODY: same a A
MISC. NOTES: the comment lines at the beginning of the worm code have been removed.
VBS.LoveLetter.I (also known as Important! Read carefully!!)
Norton AntiVirus detects as: VBS.LoveLetter.Variant
ATTACHMENT: Important.TXT.vbs
SUBJECT LINE: Important! Read carefully!!
MESSAGE BODY: Check the attached IMPORTANT coming from me!
MISC. NOTES: new comment line at the beginning: by: BrainStorm / @ElectronicSouls. It also copies the files ESKernel32.vbs & ES32DLL.vbs, and MIRC script comments referring to BrainStorm and ElectronicSouls and sends IMPORTANT.HTM to the chat room.
VBS.LoveLetter.J
Norton AntiVirus detects as: VBS.LoveLetter.Variant
ATTACHMENT: protect.vbs
SUBJECT LINE: Virus ALERT!!!
MESSAGE BODY: Largely the same as the G variant.
MISC. NOTES: This appears to be a slight modification of the G variant.
VBS.LoveLetter.K
Norton AntiVirus detects as: VBS.LoveLetter.Variant
ATTACHMENT: Virus-Protection-Instructions.vbs
SUBJECT LINE: How to protect yourself from the IL0VEY0U bug!
MESSAGE BODY: Here's the easy way to fix the love virus.
MISC. NOTES:
VBS.LoveLetter.L (I Cant Believe This!!!)
Norton AntiVirus detects as: VBS.LoveLetter.Variant
ATTACHMENT: KillEmAll.TXT.VBS
SUBJECT LINE: I Cant Believe This!!!
MESSAGE BODY: I Cant Believe I have Just Recieved This Hate Email .. Take A Look!
MISC. NOTES: comment has phrase/words: Killer, by MePhiston, replaces GIF & BMP instead of JPG & JPEG, hides WAV & MID instead of MP3 & MP2. NO IRC routine, there it will not infect chat room users. Copies KILER.HTM, KILLER2.VBS, KILLER1.VBS to the hard disk.
VBS.LoveLetter.M (Arab Air)
Norton AntiVirus detects as: VBS.LoveLetter.Variant
ATTACHMENT: ArabAir.TXT.vbs
SUBJECT LINE: Thank You For Flying With Arab Airlines
MESSAGE BODY: Please check if the bill is correct, by opening the attached file
MISC. NOTES: Replaces DLL & EXE files instead of JPG & JPEG. Hides SYS & DLL files instead of MP3 & MP2. Copies no-hate-FOR-YOU.HTM to the hard disk.
VBS.LoveLetter.N (also known as Variant Test)
Norton AntiVirus detects as: VBS.LoveLetter.Variant
ATTACHMENT: IMPORTANT.TXT.vbs
SUBJECT LINE: Variant Test
MESSAGE BODY: This is a variant to the vbs virus.
MISC. NOTES: Copies itself as sndvol32.vbs and IEAKDLL.vbs. Internet Explorer start page changed to http://altalavista.box.sk. It does not download the password stealing trojan. Overwrites *.mpg, *.mpeg, *.avi, *.qt, *.qtm. Sends the file important.htm into Internet chat rooms via mIRC.
VBS.LoveLetter.O (same as A version)
Norton AntiVirus detects as: VBS.LoveLetter.Variant
ATTACHMENT: LOVE-LETTER-FOR-YOU.TXT.vbs
SUBJECT LINE: ILOVEYOU
MESSAGE BODY: kindly check the attached LOVELETTER coming from me.
MISC. NOTES: The file script.ini, which it sends into Internet chat rooms, has a modified comment line.
VBS.LoveLetter.P (also known as Yeah Yeah)
Norton AntiVirus detects as: VBS.LoveLetter.Variant
ATTACHMENT: Vir-Killer.vbs
SUBJECT LINE: Yeah, Yeah another time to DEATH...
MESSAGE BODY: This is the Killer for VBS.LOVE-LETTER.WORM.
MISC. NOTES: Sets the Internet Explorer start page to http://www.yahoo.com/Vir-Killer.exe. It does not download the password stealing trojan. Overwrites *.ZIP and *.RAR files instead of *.JPG and *.JPEG file. Hides *.PAS and *.ASM files instead of *.MP3 and *.MP2
VBS.LoveLetter.Q (also known as LOOK!)
Norton AntiVirus detects as: VBS.LoveLetter.Variant
ATTACHMENT: LOOK.vbs
SUBJECT LINE: LOOK!
MESSAGE BODY: hehe...check this out.
MISC. NOTES: Copies itself as MSUser32.vbs and User32DLL.vbs. Overwrites *.XLS and *.MDB files instead of *.JPG and *.JPEG. Hides *.EXE and *.LNK instead of *.MP3 and *.MP2. Creates LOOK.HTM
VBS.LoveLetter.R (also known as Bewerbung)
Norton AntiVirus detects as: VBS.LoveLetter.Variant
ATTACHMENT: BEWERBUNG.TXT.vbs
SUBJECT LINE: Bewerbung Kreolina
MESSAGE BODY: Sehr geehrte Damen und Herren!
MISC. NOTES: IRC sends BEWERBUNG.HTM into connected Internet chat room.
VBS.LoveLetter.S (same as A version)
Norton AntiVirus detects as: VBS.LoveLetter.Variant
ATTACHMENT: LOVE-LETTER-FOR-YOU.TXT.vbs
SUBJECT LINE: ILOVEYOU
MESSAGE BODY: kindly check the attached LOVELETTER coming from me.
MISC. NOTES: Several comment lines have been added
This is an Internet worm, which
uses MAPI to propagate. This worm arrives as an executable with icon like
Pokemon character, Pikachu 
Once executed it modifies Autoexec.bat such that files in certain directories are deleted when the computer is rebooted. It displays graphic with text as "Between millions of people around the world i found you. Don't forget to remember this day every time MY FRIEND!". And It also sends out unsolicited email messages to all addresses in the infected users MS Outlook Address Book.
Subject: Pikachu Pokemon
Body:
Great Friend!
Pikachu from Pokemon Theme have some friendly words to say.
Visit Pikachu at http://www.pikachu.com
See you.
Attachment: Pikachu icon
Delete or ignore messages matching this description.
PS, Please open the attached file to see the sample file.
W97M.Melissa.BG is a Word 97 macro virus that has a payload of deleting necessary system files. It also sends itself out through e-mail using Microsoft outlook.
The subject of the e-mail is "Resume - Janet Simons".
Virus Characteristics
---------------begin copy of email--------
Subject: Resume - Janet Simons
To: Director of Sales/Marketing,
Attached is my resume with a list of references contained within.
Please feel free to call or email me if you have any further questions
regarding my experience. I am looking forward to hearing from you.
Sincerely,
Janet Simons.
«Explorer.doc»
-----------------end copy of email--------
If the file EXPLORER.DOC is opened, it will forward an email all entries in all available address books.
As if this wasn't enough, this trojan will wait for the user to close the document before continuing with a more damaging payload.
Please delete it!!!
W95.Hybris or TROJ_HYBRIS.C is a worm that spreads by email as an attachment to outgoing email messages.
Once the infected worm executed. This worm monitors internet access from the infected computer and monitors any email sent and received. Once it detects Internet connection, it sends an additional email to all addresses that were sent to infected user.
A sample of the email is as follows:
Subject:
Snowwhite and the Seven Dwarfs - The REAL story!" orAttachment: May have one of several different names, including, but not limited to the following:
Joke.exe
dwarf4you.exe
atchim.exe
sexy virgin.scr
enano porno(.scr
dunga.scr
branca de neve.scr
midgets.scr
TROJ_MYBABYPIC.A is currently spreading in the wild. This Trojan propagates via MS Outlook as an EXE attachment.
A sample of the email is as follows:
Subject: My Babypic
Body: Its my animated baby picture!!!
Attachment: MYBABYPIC.EXE
When the EXE file is executed, a message box with the picture of a child is displayed. When this message box is closed, the Trojan drops several copies of itself in the Windows/System directory and adds several registry entries to enable it to execute at each Windows start up. This Trojan needs Windows Scripting Host to function and upon execution tries to connect to a certain web site. In addition to this, the Trojan code also has some destructive payloads, that range from overwriting files with certain extensions to deleting certain files.
This Trojan also sends copies of itself via MS Outlook to all lists in the infected user's address book, including the infected user.
At certain times, the worm may attempt to connect to http://www.youvebeenhack.com.
The Trojan also abruptly enables/disables the Numlock, ScrollLock and CapsLock key.
Alert: Medium
TROJ_NAKEDWIFE, a new Trojan is currently in the wild and is spreading rapidly. Upon execution, this Trojan deletes all DLL, INI, EXE, BMP and COM files in the Windows and system directories. It propagates via MS Outlook, by sending out an email to every email address listed in the infected user's address book. A sample of this email is as follows:
Subject: FW: Naked Wife
Message Body: > My wife never look like that :)
Best Regards,
<Sender>
Attachment: NakedWife.exe
Once the attachment is executed, This worm masquerades as a Flash movie. When run, it sends itself to all recipients in the Outlook Address Book. and deletes all .BMP, .COM, .DLL, .EXE, .INI, and .LOG files in the WINDOWS and WINDOWS\SYSTEM directories. After all files have been deleted
- You system will be inability to launch any applications.
VBS_STAPLE.A is a new Visual
Basic Script virus that is currently in the wild. Upon execution, this
virus displays a message box and then sends itself out via email to the
first 50 recipients listed in the address book of the infected user. A
sample of the email is as follows:
Subject: RE:Injustice This virus also sends the above email to certain email addresses and
then tries to access some web sites using Internet Explorer. Upon execution, this Visual Basic Script virus drops a copy of itself
in the Windows System directory and displays a message box titled
"HELP US TO STOP THE BLOOD SHED!!" with the following text: PLEASE ACCEPT MY APOLOGIES FOR DISTURBING YOU. Then it sends itself out as an email attachment via Microsoft Outlook
to the first 50 recipients in the address book of the infected user. A
sample of the email is as follows:
Message Body:
Dear <Outlook Username>;
Did you send the attached message, I was not expecting this from you !
Attachment: INJUSTICE.TXT.VBS
Remember that one day YOU may be in this situation. We need every possible
help. Israeli soldiers killed in cold blood 12 year old Palestinian child
Mohammad Al-Durra, as his father tried to protect him in vain with his own
body. As a result of the indiscriminate and excessive use of machine gun
fire by Israeli soldiers, journalists and bystanders watched helplessly as
the child was savagely murdered. Palestinian Red Crescent Society medic
Bassam Balbeisi attempted to intervene and spare the child's life but live
ammunition to his chest by Israeli fire took his life in the process. The
child and the medic were grotesquely murdered in cold blood. Mohammad's
father, Jamal, was critically injured and permanently paralyzed.
Similarly, approximately 40 children were slain, without the media taking
notice or covering these tragedies.
THESE CRIMINAL ACTS CANNOT BE FORGIVEN OR FORGOTTEN!!!! HELP US TO STOP
THE BLOOD SHED!!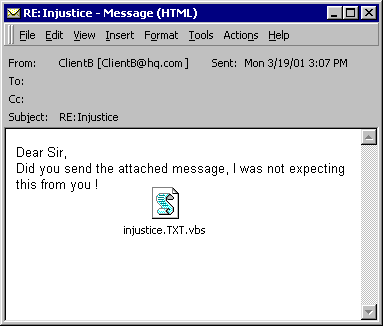
Risk Type: High
This Trojan is currently in the wild and comes disguised as a Love
Matching program. It was created in Visual Basic 6.0 and uses the Visual
Basic component Microsoft Script Control to propagate using the default
installed mail client. It finds recipients to receive the tainted email
from the Windows Address book of the infected system. A sample of the
email is as follows:
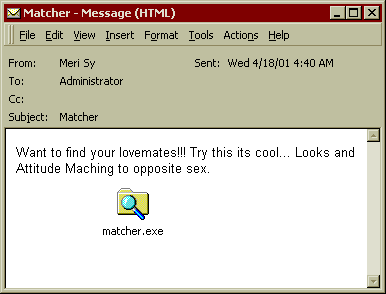
Subject: Matcher
Message Body: Want to find your love mates!! Try this its cool… Looks and Attitude Matching to opposite sex.
Attachment: Matcher.exe
The worm then sends itself to everyone in the Outlook Address book with the above email. The worm will continue to send emails in an infinite loop.
Delete all detected files.
VBS.VBSWG2.X@mm is an encrypted VBScript worm that uses a known exploit to send itself to all recipients in an infected user's Microsoft Outlook address book. It also has the payload that opens a Web site that contains pornographic contents.
Also known as : VBS.VBSWG2.D@mm, VBS.HomePage
Trigger condition: Upon execution
The email message has the following characteristics:
Subject: "Homepage"
Body:
Hi!
You've got to see this
page! It's really cool ;O)
Attachment: Homepage.HTML.vbs
Prior to mailing itself out, the worm searches for email messages with the
Subject of "Homepage"; it deleted these messages.
The worm pretends to open a Web page upon execution. It randomly selects
one of four pornographic Web pages.
This particular email message is
a hoax. You might receive it in the near future. It has been reported that
the SULFNBK hoax email has been propagated wildly. HQ MIS requests that all
ASI email users not to propagate this email. This hoax warns against a
virus contained in a file called SULFNBK.EXE, that arrives hidden in an
email message. SULFNBK.EXE is a normal file that is installed with the Windows Operation
System.
.
This file in not destructive.
A sample of the email is as follows:
Original Portuguese version:
Vocês acreditam que uma amiga da lista enviou um alerta e os procedimentos
que deveriam ser tomados para a possível detecção do maledeto SULFNBK.EXE. e
eu fui conferir só por desencargo de consciência. Pois é...O bichinho tava
lá, escondidinho até da McAfee e do Norton, talvez esperando algum gatilho
prá começar a trabalhar, né?
Aí vão, moçada, as orientações que eu segui à risca e que me levaram ao tal
coisinha ruím:
1 - Iniciar/Localizar Pastas. Digite o nome do "mardito": SULFNBK.EXE
2 - Se for encontrado, abra o Windows Explorer, vá até a pasta onde ele se
encontra alojado e delete-o de lá ou do próprio ambiente do Localizar; - Não
click com o botão esquerdo sobre ele e não abra o arquivo nem em caso de
incêndio, ok?
3 - Apenas delete o bichinho.
4 - O meu estava em Windows/Command.
5 - O vírus da pessoa que passou o aviso estava em Windows/Config.
Sim, o Norton e nem o McAfee não detectou.
Não sabemos se ele faz algum estrago na máquina, mas acho que ninguém aqui
vai querer testar para saber, né?
Gente, sem brincadeiras, já tirei o meu daqui....
E nem imaginava que tivesse hóspedes no PC.
Minha vacina está super-atualizada!!!
Façam o mesmo, ok?
Translated English version:
Do you believe that a friend of mine sent me an alert and the procedure that
we have to follow for the possible infection of SULFNBK.EXE. And I had
checked, just to make sure. An then... the file was there, hidden even of
McAfee and Norton, maybe waiting something to start work.
Well, see bellow the procedure that I followed step by step, and I found the
file:
1. Start/Find Folders. Type the file name: SULFNBK.EXE
2. If it find, open Windows Explorer, browse into the folder where the file
is and delete it. Do not click with left button on the file and do not open
it.
3. Just delete it
4. Mine was on Windows/Command
5. The virus from the person who gave the alert was on Windows/Config
Yes, Norton and McAfee do not detect it.
We do not know if it makes some damage on the machine, but I think that
anybody will not want to test it to know, will it?
Folks, this is not a fun, I delete it from my computer.
And my definitions are updated.
Do it the same, ok?
SirCam virus has ranked the top number one virus among all other viruses. Please be really careful on what you receive in the near future.
HQ MIS be able to collect more information about this wild spread virus in the Northern America.
First of all, this worm arrives as an email attachment having two extension names. Such as Filename.EX1.EX2 Filename.EX1 is random file chosen from an infected user's personal folder such as "My Document". EX2, can be a EXE, PIF or LNK extension.
Secondary, The body of the email will always begin with "Hi! How are you?" and end with "See you later. Thanks." In between these opening and closing lines will be one of the following:
HQ MIS has a place the SirCam remover tool at //Intra/IT Download Center/Virus Removal Tool/Sircam remover.
Thanks to Brian Paterson and Monson Chan provided sample of the virus email.