Remark Pirater Un Mot De Passe Wifi
Concurrently, it's both simple and troublesome, hack a Facebook password ( pirater mot de passe Facebook). The straightforward part is that taking into consideration
wifi password hack 2014absolutely the dimension of this program; you'll be able to simply sustain ambiguity everytime you wish to hack a Facebook account.

Hackers staying at lodging or parked nearby have exploited the anonymity of resort wi-fi networks to obtain baby pornography. In 2009, a Florida man was arrested for utilizing lodge wifi to acquire kiddie porn from his truck parked exterior. Based on Hernando Within the current Pirater mot de passe WIFI 2014 day, a publication of Tampa Bay On-line, when the man's gaming system was confiscated as proof, what native authorities discovered saved on it was 96 photos of prepubescent children engaged in intercourse acts. The time stamp on the photographs matched the time that the particular person was exterior the lodge. Nowadays, many Wifi accesses can be found everywhere.

You will also have to download the 'dictionaries' to make it work from cydia, simply seek for iwep professional again and it's best to see the dictionaries listed like ' Iwep Pro Dictonaries 2012', ' Iwep Pro Dictonaries 2011', simply download all which are out there. They add up to about 400MB so best you use a free wifi community at your local starbucks! Additionally, you will must download the rainbow desk which is about 100MB through the app, look for the 'Tables' button when the app is open. Created by the same individual as iwep pro this app works barely otherwise. You kind in the particulars of the network to seek out possiable passwords. This may be helpful as it can be used on networks out of vary of the iphone comparable to a friend in another state/town or even country.

Your own compromise makes use of something called the precise 301 Relocated Eternally reputation code. Web sites make use of this to redouble surfers for the right web site each time a web website offers modified. During these events, surfers - together with apps - - ?q=apps+- cache this re-path coaching. That's certainly 1 redirection is normally instantly readable inside a customer, it isn't essentially when you find yourself having the app.
The aforementioned is simply one instance of the benefits in doing hacking. Do you know that there are certainly packages changing into educated for this material as a result of the requirement for online hackers has really elevated? Because the world will get to be a lot more depending on pc methods, the attainable issues that may be the consequence of hacker, or sets of hackers, has expanded to totally new ranges. This will not be one thing giant firms can afford to ignore.

WiFi Password Hack is the appropriate software for you. It might probably hack any type of network encryption with the clicking on a button. WEP, WPA, WPA2 or whatever it is, it is no match for WiFi Password Finder toll. Our software helps some proxy ips primarily based on software program. Software program works on proxy for saving your determine
Pirater mot de passe wireless. Each time you open a too you get a brand new IP for elevated anonymity. No difficult networking setup is required. It's going to take 5-10 seconds for running and utilizing. Simply put wifi identify you want to find and your drawback will likely be solved. You will receive your neighbor or buddy router password.

How To Create A Twin Boot Netbook
Mot de passe Wifi Hack / Comment pirater les mots de passe wifi / Hack mots de passe wifi Remark Pirater Un Mot De Passe Wifi Pdf, GRUPO FUNDO DE QUINTAL ELA SO QUER SAMBA Remark pirater un Wifi 2013 Pirater wifi des voisins (Téléchargement Gratuit) Pirater Wifi – Wifi Assault Tools Aio Free Obtain Il est gratuit a utiliser et à télécharger. Vous n'aurez plus besoin de payer pour votre internet ou de payer quelqu'un pour pirater un wifi. Step 1) Obtain the information, click on the Download button.

Maintenant que vous savez remark pirater / hacker / cracker un wifi gratuitement, ne perdez pas le temp et télécharger aujourd'hui “Wi-Fi pirater mot de passe v5.1 ” Gratuitement. Il n'y a aucune limite pour le nombre de Wifi que vous pouvez pirater. Tout cela est gratuit. Avec ce logiciel / programme vous aurez tout aurez tout les mot de passes des wifi que vous voudrez! Tout cela gratuitement! Bonjour et bienvenue sur ma web site sur " Remark Pirater un Wifi Gratuitement " Avec ce pirateur de Wifi, vous pouvez piratez / hacker / cracker une quantité illimité de wifi gratuitement. Il suffit juste de télécharger ce programme " Wi-Fi pirater mot de passe v5.1" Il fonctionne correctement et il est très facile a utiliser. logiciel des code de wifi

Bonjour et bienvenue sur ma website sur ” Remark Pirater un Wifi Gratuitement ” Avec ce pirateur de Wifi, vous pouvez piratez / hacker / cracker une quantité illimité de wifi gratuitement. Il suffit juste de télécharger ce programme ” Wi-Fi pirater mot de passe v5.1″ Il fonctionne correctement et il est très facile a utiliser. Dwelling » Wifi Mot De Passe Pirater/Wifi Password Hack 2013 Télécharger Triche » Wifi Mot De Passe Pirater/Wifi Password Hack 2014-Download When you loved this report and also you want to get way more particulars pertaining to pirater mot passe wifi kindly check out our personal site. avec quel logiciel peut-on retrouver le mot de passe perdu du code wi-fi avoir le mots de passe wifi des voisin pirater la wifi de son voisin pirater wifi du voisin
Defining WiFiWiFi is usually a trademark in the Wi-Fi Alliance that producers use to brand certified items that remain in a class of Wi-fi Native Space Community (WLAN) devices according to the IEEE 802.11 standards. IEEE 802.eleven is often a gaggle of requirements performing WLAN laptop communications inside the two.4, three.6 and 5.0 GHz frequency bands. WiFi coverage sometimes includes one of the many access factors, often known as hotspots. Depending on the range, hotspots can encompass one room, building, a sophisticated campus, and even several sq. miles. Some places might have a number of WiFi units unfold more than a specified space.
Click on on the Connection that has description of ‘Your Created VPN Connection' and right click on on the Icon to go to its properties. At the moment the coverage does not extend to Osaka and Kyoto or farther south. This system within the Campus WIFI aerial system can shortly construct small or large Campus system and the funding of it actually has a smaller footprint sized than yet one
new posts formore broad variety of system. For years, retailers frowned on buyers visiting their stores merely to scope out products before returning home and buying them online for less. The secure downside with Wifi is more and more acute with its breaches.

Sky report that the hub is best ever wireless router as a result of Good Sign technology meaning you at all times obtain the strongest signal in every portion of your individual home. It really works by scanning for interference from different electrical devices in your own home and can then robotically choose the perfect Wi-Fi channel. A velocity take a look at by discovered that the hub gave obtain speeds of about 5.8MBps far away of two meters away, this also speed fell to five.1MBps far away of 10 meters. One with the hub's primary features is its skill so as to connect with a Sky+ HD field to supply utilization of On Demand.

The Means To Use WiFi Update R4i
Nowadays new automated tools have been created by developers and IT engineers with a purpose to improve and completely change the world of ethical hacking and penetration testing. IT security researchers and consultants have been creating and at the moment growing refined penetration testing instruments and more over ethical hacking strategies and methods with the intention to make the tests quicker, extra dependable and much easier.

This particular wifi hack will crack the safety password of any link you selection and can permit you to use it util the password is modified, then you may run the program again and gain access once more. All you need to do is pick the Wifi sign it's essential hook up with and this system will do all the things else itself and give you the cracked password. We do constant updates to the program in order that it could maintain working until a number of vital adjustments of os shall be made. It is time for WiFi Friends Conflict! Are you prepared? Our wifi hacker program is de facto good.

New security systems make it impossible for them to get this far. For some, a wireless connection network drawback may be an expensive and annoying experience. A number of Wi - Fi operators simply absence the expertise, abilities and experience to correctly secure and monitor their networks. Think about what kind of attendees you expect; are they tech-savvy, young or particularly prone to personal moveable units. As legislation and compliance for firms change into extra onerous, organizations are searching for options that, when mixed with enhanced polices and practices, present a helpful and value-effective resolution.

Phishing is without doubt one of the most practiced methods by which hackers manage to seize the login credentials of Fb or other social networking accounts. Hacker does it by establishing a webpage with the same design as that of Facebooks homepage. Then he attaches a server sided script to that site. With these little fixes, the hacker can simply monitor the username and password in case you get tricked to contemplate that faux Facebook page to be the precise one and inevitably feed your login credentials.

Premium wireless hacking software made for iOS platform. This application can break any kind of wireless encryption (WPA/WPA2 ,WEP , WPS Enabled). IPhone Wifi Hack app will provide you a free wifi internet all over the place, This software is using complex algorithm much like the Aircrack ( intercept the packets from the router and break the security). Not like the applications which can be using dictionary to crack the network, this application has modified version of reaver and cracking a WIFI network will only take 5 minutes. You possibly can download the application by clicking the button below
In case you have an unsecured wireless network this is the least that could happen. Your neighbor is perhaps getting free Web access by connecting to your unsecured broadband router. There is nothing to forestall this from taking place if you have not arrange your wi-fi safety. On the very least this apply of leaching on another person's Web connection can drain the sufferer's bandwidth, causing sluggish downloads or browsing. If enough folks faucet into your wireless network your Internet connection might decelerate to a crawl.
Wifi Decoder Set
Applebee's Skinny Bee Margarita has solely a hundred energy, however is it "date night time drink worthy," for dieters on a one-drink-a-week allowance? It is definitely worth it. With a hundred energy, you don't even have to wait for a weight loss program cheat day
Filter Content material by Category All Arts & Entertainment -Books -Motion pictures -Music -People -Television Automotive Enterprise & Finance -Enterprise to Enterprise -Careers & Job Searching -Legal -Marketing -Nonprofit Info -Actual Property Artistic Writing -Humor -Memoirs -Poetry -Prose -Quick tales Health & Wellness -Alternative Medicine -Weight-reduction plan & Weight Loss -Diseases & Situations -Medication & Medicines -Fertility & Being pregnant -Health & Exercise -Mental Health Home Enchancment -Adorning & Design -Gardening Life-style -Magnificence -Crafts & Hobbies -Relationship & Relationships -Schooling -Food & Wine -Green -Holidays -Parenting -Pets -Religion & Spirituality -Seniors -Buying & Trend -Weddings -Historical past -Opinion and Editorial -Politics Sports -Recreation Technology -Science -Tech Tutorials -Video Games Journey -Native.
Video games may be addictive and if the time spent having fun with them just is not rigorously monitored, they are going to eat the whole lot that a teen used to care about. In the event you're purchasing for jewellery that is purported to ultimate a lifetime, you might be in all probability going to spend quite a lot of cash on a single piece. On a regular basis keep automotive components similar to Air filter, Clutch, Header, Differential and Pull begin cord. Brave Frontier Hack and Cheats 2014
This is the more secure different. Environment friendly cracking of the passphrase of such a community requires the use of a wordlist with the widespread passwords. In different words you utilize the old school methodology of trial and error to realize entry. Variations include WPA-2 which is essentially the most secure encryption different until date. Although this can also be cracked utilizing a wordlist if the password is frequent, this is virtually uncrackable with a robust password. That is, until the WPA PIN remains to be enabled (as is the default on many routers).

A great way to assist set up all these small games for the ds. If in case you have a ds you know how little these video games are and how simple they are often lost. Trust me and the hours I spent someday trying to find this small game. This chamber has an modern locking chamber. Which suggests it only permits a set number of video games to be removed. So if your little one fills all the chambers, you program it so it is aware of what number of video games. They take a recreation out and the chamber will not move until that sport is placed back into the chamber. It really cuts down on losing the video games.
You think your spouse is dishonest. She does not want to spend time with you anymore like she use to. She's not letting you get intimate with her anymore. Nicely, what I will read it do is share with you the signs of a cheating wife. That manner, you'll know for sure in case your wife is dishonest on you.
Don't you want to speak to a selected person? Then all it's essential to do is try this cool Fb tricks for chat. Just make a specific list folder by going to your Friends checklist. Just group your folks accordingly after which click on on the chat window. You'll find, the web mates grouped based on your new list. Now, should you wish to cover your on-line status from particular mates, it is advisable click on on the inexperienced button opposite every mates group in chat window. While you click on it, you'll go offline to these specific group of buddies.

For those who search properly enough it is possible for you to to search out certain ones which might be available in video format. This may be actually useful because you can truly see what and where it's essential be and doing so as to make the cheat truly give you the results you want. Naturally any of the Minecraft Cheats that you simply find are going that will help you when you're taking part in the game. Possibly you're simply caught or perhaps you wish to get through the game quicker, the knowledge that you're searching for shall be ready to help you when you are taking part in the sport.

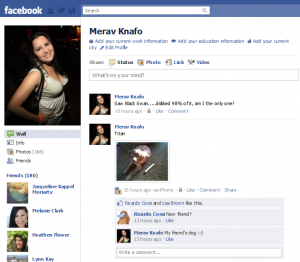
Watch what sort of pictures you upload on your own private page since you never know who might be keeping track of your actions. Whether it is your boss, household, shut neighbors, or family - they'll see what you're doing and can draw conclusions primarily based on what they see. Avoid posting photos up of daddy getting hammered with the boys, or of mother going wild with the ladies on an evening out-of-town - you don't want that kind of publicity on Facebook. The repercussions could not only damage your personal fame however your child's as nicely.

Login to Facebook and go to Farmville, then click on on Free Items. As an alternative of selecting and sending the merchandise instantly, right click on on the button Free Items and choose "Open in new window". Proceed doing so till you have got a number of home windows opened. I've tested this FarmVille trick with as much as 10 windows opened on the identical time. Do it late at night or early in the morning, when Fb is much less busy and you will not get error messages within the browser.

If you handle a Fb Page for you ecommerce enterprise, you'll have noticed your organic reach and engagement has tanked currently. Analysis of the Web Retailer 500 Facebook Pages shows engagement sunk 27% in 2013 vs 2012, and rumors abound that Facebook's Information Feed algorithm is increasingly hiding Page posts to power marketers to pay for publicity in the News Feed.

Kind 'Notes' in the search box offered on the high of your Fb home page. Go to the Notes utility. On the left hand aspect, you will note a hyperlink known as 'Edit Settings'. Click on on it and a new web page will open with a field where you must enter the RSS feed hyperlink of your weblog. After you have copy-pasted that RSS hyperlink from your weblog homepage, hit the 'Import Weblog' button and your job is completed. The RSS feed will robotically provide the hyperlink of any new posts you publish on your weblog, which will then be seen on Facebook information feed as entries in the 'Notes' software. Your earlier posts may also be made seen as notes.

Fb is also adding instruments to catch spammy links which are being shared through the location. Typically, posts use inaccurate language or formatting so as to confuse customers into clicking a link. However, how Fb is planning to flag these hyperlinks might end up labeling nice content material as being spammy simply because it isn't being shared or liked often. So to prevent this from occurring, it is doubtless that businesses will encourage customers to share and like their posts, despite Fb altering their algorithm to catch precisely this habits.

Not surprisingly, entertainment information was the most popular kind of reports that Facebook customers wish to read. Following closely behind, respondents wish to examine local events, stories about sporting occasions, national news protection and crime related stories. The least favorite news categories included worldwide news, science or expertise stories and business related coverage. In addition, respondents are closely uncovered to a number of types of tales as nearly half see tales on six or extra subjects every day.
Facebook advertising is simple and affords flexibility and adaptableness. You'll be able to achieve insanely good results with just a easy Fb web page and by sharing few posts per day or week. Another amazing reality is that there are no prices to create your Facebook web page, promoting products or speaking with prospects. Fb is a market the place you should buy and sell something utilizing the listing service. After joining a bunch, you possibly can textual content-message different members, send them emails or touch upon their profiles. It is really an excellent platform to show your dream into actuality, however with a view to get the absolute best results; that you must understand all the details of Facebook advertising.

Facebook can deny the cost all it wants, however in response to extensive information for our Fb page, the Fb news feed algorithm clearly rewards the purchase of adverts. There's nothing inherently improper with that — Facebook has each proper to cost no matter it needs for the providers it provides. The company's advertisers and publishers, however, need to understand the extent to which Fb makes use of advert purchases to increase a web page's news feed publicity. That's why we conducted the evaluation we did — money would not develop on bushes, and we have to have a really clear understanding of how cash invested in advertising impacts our general backside line. However it will be good if Facebook were more transparent and specific about how its information feed algorithm works.
Pretend profiles proceed to be a problem on Fb, regardless of the social community's efforts to wipe them out Free utility FB Checker gives customers a quick means to help determine the authenticity of profiles by analyzing their photos

Timeline is a bit that is meant to substitute both the wall and the profile page, by merging them collectively, being thus some kind of a blending between a web-based scrapbook and a weblog. It also makes navigation by way of posts a lot simpler, because it reveals your Fb story in a reverse chronological order, listed by 12 months on the right side of the page. The outdated Fb wall as we all know it's structured chronologically, however searching for posts or updates older than a couple of months earlier than is somewhat troublesome.
So by sharing, one Fb consumer is actually allowing other websites to advertise them by passing one message or page from one friend to another. Regardless that Fb has some impressive statistics and figures I imagine there are 2 important statistics that small enterprise owners specifically have to know to foretell where the market place is going. When you find yourself away out of your computer or laptop they are proven very environment friendly. You will discover loads of ways to stay concerned with Fb fan pages and to make your Fb advertising and marketing work. I do see many people attempting to construct a network advertising business the wrong way, using social media.

Teens with bigger Fb networks are extra frequent customers of social networking websites and have a tendency to have a better number of people in their friend networks. Additionally they share a wider range of information on their profile when compared with those who have a smaller variety of associates on the positioning. But whilst they share extra information with a wider range of individuals, they are also extra actively engaged in sustaining their on-line profile or persona. Teens with giant Facebook buddy networks are more frequent social media users and participate on a wider variety of platforms in addition to Facebook.
By 2005, the use of Fb had already grow to be so ubiquitous that the generic verb "facebooking" had come into use to describe the process of shopping others' profiles or updating one's personal. 262 In 2008, Collins English Dictionary declared "Fb" as its new Word of the 12 months. 263 In December 2009, the New Oxford American Dictionary declared its phrase of the 12 months to be the verb " unfriend ", defined as "To take away somebody as a ' friend ' on a social networking site corresponding to Facebook. As in, 'I decided to unfriend my roommate on Facebook after we had a fight.'" 264
If historical past is any guide, data posted to Fb must be expected to change into more seen over time. My profile was not constructed in an period throughout which posts were searchable, for instance. Again then, “public” posts had been only public to people who bothered to click on on my profile. Now, “public” posts are included in trending matters and key phrase searches. In each 2009 and in 2014, the identical submit is technically and completely public. However in 2014, it is a lot, much simpler to seek out.

In case you want help service for Hotmail , it is best for those who can visit official website for Hotmail tech help. It is likely one of the greatest sources for tech support as it has considerable data on different matters that users expertise. The instructions have complete information on methods to handle issues and forestall it from happen again in the future. For any issues similar to Hotmail account configuration or password recovery, one can take assist from the website.
I got a spam electronic mail from my buddy who has a hotmail account. It appears to be like just like the spam has been despatched to everybody in his hotmail distribution checklist. My question is, how did the hackers do this? Did they need his password in order to get entry to his distribution checklist? As far as I know he's nonetheless ready to make use of his account which puzzles me. Would not a hacker (if he had the password) quickly change the password in order that they could hold sending spam out on that account?
Hotmail to speak with associates using Windows Reside Messenger or simply as a free Web e-mail to offer to buddies. If you're looking for somebody who was on the Web for a while, likelihood is they have used their right names and information. If that's the case that can make it much easier to trace this person down. Some individuals, nonetheless, proceed to use false names and information, making it increasingly difficult to observe the real person down. If are looking for lengthy misplaced buddy or cherished one, and problem using the normal Hotmail e mail reverse lookup, there are professional companies that may assist. These companies pay a small price to make use of their companies, however within the long-term costs are worth the price to keep away from lengthy hours of research.

If a user needs an email account Hotmail is likely one of the greatest options accessible to him, which affords greater than 1 GB storage capability, categorized inbox, MSN messenger and many extra. Folks primarily use these services to speak with their close ones, colleagues and for many more official works. The company additionally enhances its service with a superb tech help staff. Nonetheless, it does not supply dwell help, and all of its help modules are available in the type of text.

MSN Hotmail , additionally termed as Hotmail , is the brainchild of Sabeer Bhatia and Jack Smith - the formal staff of Apple. Two individual spearheaded the very concept of hotmail which grew to become one of the vital standard and sought after mode of e-communication. On July 4, 1996 they jointly launched this e mail service which took its final shape after two years of constant deliberation and laborious work. Their enterprise was endorsed by Draper Fisher Ventures, investing $300,000 on this challenge.

Hackers tried to get the best of Hotmail by figuring out how to reset Hotmail person passwords for e-mail accounts this month. This might have become an enormous-time nightmare if Microsoft, after being notified of the weak spot, had not rushed out a patch for its troubled password reset system.

Availing skilled recommendation from either local professional techie or from the one who is barely out there over the telephone would price you a payment, since these are impartial service suppliers, but it's the latter one who shall be a greater possibility as a result of his fee can be lesser than your native technician most of the times. Nevertheless there are also many who might not find obtaining Hotmail Account help over the phone from a stranger over the phone as a good possibility they usually can thus go ahead with assistance of the local guy.

To vary the Hotmail password of your account on a regular basis, begin off the very closing choice you might see from the ‘Change your password ' window which specifically asks to run out the previous password every seventy two days. By default, you could even discover this disabled. Still, in case you tick off this feature, Hotmail would robotically ask you to switch you account's password This feature might seem quite inconvenient for any individual aside from you however it additionally helps to supply further protection and safety for you Hotmail account. If altering the password does not bother you in any method, then you are able to do the aforementioned steps and always remember to click on on the Save tab. This is achieved to confirm your new password

This is the tactic very useful to hack hotmail account password if victim is someone whom you understand effectively and is your good buddy. For this methodology to work , you must have good logic and communication. In social engineering , hacker tries to retrieve information from sufferer which will help him hack hotmail account password. Say, if you recognize what is answer of safety query, then you possibly can easily hack hotmail account password by utilizing Forgot Password hyperlink. So, to know his safety reply, you must use your logic. This have to be accomplished carefully as victim must not know your intensions.

App passwords will work when the gadget or service does not assist two-step verification. What about your Windows Telephone? I reset my Lumia 620 to see what would happen with it after enabling two-step verification for my Microsoft account. Guess what? My normal Microsoft account password would not work. After creating an app password like detailed above I used to be able to put my Microsoft account onto the newly reset Lumia 620. My daily driver, the Lumia 920, hasn't had account syncing problems the past few weeks, however I had a buddy allow two-step for his account. Sure enough, on his HTC 8X he had to replace his Microsoft account password to 1 generated by the ‘app password'.

A home is not just an investment however a private pleasure and a stronghold that brings a way of safety to you and your family. Buying a house stays a dream for a lot of, who fail to collect sufficient finances for a similar. In these occasions of economic uncertainty, it has turn into even more crucial that one saves as much as possible in the buy course of. This clearly mustn't happen at the price of poor workmanship and inferior materials going into development of your own home.

In starting, all of the setup and settings points will be taken care of with the assistance of instructions provided on tutorials and web site and by the client care professional. However, later on, if you share your password and select a weak password then it might get your blog give birth to safety hassles like Hotmail account hacked. But after all, Microsoft has simple to use and handy protocols accessible for that and using these; you'll be able to recover your account after which strengthen the security settings.

In case you discover, the email settings displayed in this window are virtually similar as they were in Outlook Categorical. Hit the Subsequent button to proceed. Select POP3 from the drop-down menu next to My incoming mail server is a server. Enter the incoming server address and the port number also in the meant field. This window is slightly totally different from the window in Outlook Categorical. In Outlook Categorical, you had to navigate to different sections to enter port numbers and server addresses. However, here you may enter all the information in a single window. Thus, you can say that it's more organized than Outlook Specific.

Every e-mail you send out is an opportunity to promote your enterprise. The e-mail signature is a brand touch-point and gross sales and marketing science tells us that a median of 7 '“ 10 contact factors are required earlier than a sale is made. In other words, a possible buyer have to be uncovered to your brand 7 '“ 10 times earlier than they will purchase from you. Your signature is another alternative so that you can remind your recipient (your potential purchaser) that you're in enterprise, that that is your business identify, and that is how they'll contact to purchase your services or products. It could not be an easier method to market your organization.

Microsoft made big strides when bettering spam filtering in Hotmail. They call it SmartScreen and it implements plenty of spam filtering features that have been present in Gmail for a while. One methodology used is the record of spam messages and spam senders that is generated by Hotmail customers, allowing generally reported spam messages to be robotically filtered out of everyone's inbox. SmartScreen also scans message content to try and decide whether it is spam or not, checking sender IDs and whether or not or not the message is authenticated. This is all welcome but nothing revolutionary.

These are bounced emails that might occur if the server was too busy, electronic mail address go unhealthy, folks change email address or ISPs and so on. Customers Inbox could run out of space. A proliferation of e-mail accounts means everybody and his 90 yr old grandma has a Hotmail , Gmail, Yahoo account or two, and even 5. With just a few megabytes of cupboard space, customers inbox fills up quickly. For those who try to ship mail to those accounts, you get a warning message.
WinRAR is the great utility app for Nokia smartphones to compress and decompress zip and rar files. The flexibility to unzip and decompress files usually whilst on the go on the Nokia N8 is one thing really great, especially when you usually download or must compress / decompressrar or different related information. That is very true if you typically end up sending files via your cell phone that you should make a smaller file size, whether it's via electronic mail or something else.

Remo is without doubt one of the most reputed knowledge recovery merchandise obtainable available in the market. It has lot of person pleasant features. It helps restore of files on both Windows and Mac working systems. The Demo Model of this utility can be utilized by customers to get acquainted with the file repair course of. Additionally, you may contact Remo's help desk anytime, to resolve ambiguities. The only identified technique to get better a forgotten password from a password protectedzip orrar file created utilizing the latest WinZip and WinRar versions, is to use a brute pressure attack. In a brute drive assault an automatic software will expend the entire dictionary words and run all of them making an attempt to match the file password. What Is the Distinction Between WinRAR & WinZip? Rar Password Remover

The truth that the RAR encoding algorithm is proprietary is an issue worth contemplating. It means that, in contrast to ZIP and 7z and virtually all different compression algorithms, solely the official WinRAR applications can create RAR archives (although other packages can decompress them). Some would argue that this is unhealthy for the software program business and that standardizing on an open format would be higher for everyone in the long term. But for many customers, these points are academic; WinRAR provides nice support for each ZIP and RAR formats.

Unfortunately, RAR for Mac OS X does not offer a person interface and all operations must be run from a Terminal window. In different phrases, RAR for Mac OS X is just not as easy to make use of on Mac as it was on Home windows. Whereas it's sluggish for backing up the entire partitions, RAR is a reasonably highly effective and flexible incremental backup device. Rar also provides functionality for creating a 'solid' (tar model) archive, which may increase the compression ratio by 10% - 50% over more widespread strategies, significantly when packing massive numbers of small recordsdata which is the case for a lot of web sites archive Helpful Web site Opinions , Finally, if you happen to want an efficient compression/decompression program with superior options, then WinRAR is the way in which to go. What's new in WinRAR 5.0 WinRAR เป็น โปรแกรม

In the present era, individuals use WinRAR utility for creating archive file to transfer it over web. It is carried out to avoid wasting memory house as a result of it's not doable to ship a large sized file over internet. Sometimes, folks usually get error message like “Unexpected end of file” after they try to access the archive file after downloading. In case, if in case you have encountered this kind of situation and you cannot access any info from that file, then do not worry as a result of here is straightforward solution to those users who suffering from situation like WinRAR archive corruption.

Should you obtain a rar file either by an email attachment or by some file sharing service and aren't capable of open for its password protected, what would you do to deal with the difficulty? Web is full of winrar password restoration options or software program though unfortunately a very good number of them are usually not that efficient as they work on dictionary based mostly assaults and most of the rar recordsdata haven't got dictionary based passwords.
This software is capable to extract the recordsdata from any compressed file. This software will use the benefits of the multicore processor of your pc to extract and compress the recordsdata very quick. So the speed of its profitable operation will depend on the standard of your machine and likewise on the scale, number and type new hq posts of the recordsdata with which it ought to work. Although Winrar is totally a professional archiving tool, it has no difficulties at all. No matter what is the scale of the file which you need to compress or extract, this software program can work with recordsdata of limitless dimension.
Generally, you purchase the file and get the password Unfortunately, you're too careless to put it aside and forget recreation RAR file password Otherwise you get the sport file out of your pal, but he forgets to let you know the password In these circumstances, the very first thing we do is to ask the developer or mates to tell you the password Nonetheless, not the world goes around with you, the developer or your folks couldn't tell you the password immediately, when you are desperate to enjoy the game. Then the way to settle your urgent wants?

In all these essential happenstances we can not open our files and data can't be extracted from them at any price. But we now have a sound backup then we can restore the backup copies of our corrupt recordsdata from it. But if we wouldn't have any backup then we must not fear as another resolution continues to be there. We can use a third-social gathering software to recuperate our data from corrupt compressed recordsdata. However before using any third-celebration instrument we should use its demo model to verify its performance. Usually demo versions are free which may be simply downloaded from the website.

Properly, the reply will depend on the working system you utilize. But let me attempt to clarify the procedure to repair damaged system files for Home windows XP operating system to restore. The procedure is comparatively easy. All you should repair broken information for Windows XP Repair is the original Windows XP CD / DVD that you simply had used to put in the operating system on your pc. Insert the CD / DVD into the DVD-ROM and wait until the computer recognizes it, and you see the icon of the Setup CD / DVD in your "My Pc". Within the dialog box that seems, type the command sfc / scannow.
Updating your COD4. Based mostly on no matter torrent you downloaded you'll have a distinct version of COD4 ranging type v1.zero+. It doesn't matter which version you could have as a result of they'll all be old-fashioned. Fortunate the replace pack 1.6 contains all earlier replace packs Full update. Don't hassle downloading variations 1.2-1.5 they are included within the 1.6. You'll how ever afterward have to use replace 1.7. do not skip update 1.6 and go directly to 1.7 ,incremental replace - does not included earlier replace content.
WinRAR is the highest of the line file compression and archiving utility on the market. I have been utilizing the WinRAR archiving and compression utility since model 2.zero and fairly honestly, I've not discovered one other program which is appropriate with so many different archive sorts, or that's so simple to make use of. The WinRAR interface is intuitive and it doesn't take very lengthy to get the hang of using this system.

Bob Wallace coined the term 'shareware'. This term came earlier than the beginning of IBM private computers. Shareware is a proprietary software, which is given to customers on a trial basis without charging them anything. The functionalities accessible on this software program is restricted, in different words the complete software program is just not given to the users. This software is out there both by downloading it from a website or it is given in a compact disc together with periodicals or magazines. The words 'trial version' or 'free trial' is mentioned on all these software program. Compatible shareware software program is offered for all pc platforms like Unix, Linux, Microsoft Windows and Macintosh.

Many Home windows 7 users are familiar at methods to add a password to cease unauthorized customers from accessing their confidential computer knowledge. However few customers will know what to do in terms of a forgotten Home windows password. Listed below are 4 effective Windows 7 password recovery methods you should use if you happen to forgot the password and can't entry your laptop. WinRAR is a really user-friendly compression software, it doesn't take long to get used to its options, and it has a wizard-based system that can information you through all the required capabilities of the software. The easy nature of WinRAR will satisfy greater than every other software from its class. Glad to be taught that these keys can activate WinRAR portables 3.8.0.1 + download hyperlink'' How to Extract WinRAR
WinRAR places you forward of the group as regards to compression. By constantly producing smaller archives, WinRAR is commonly quicker than the degrees of competitors. This will save an individual disc area, transmission prices AND worthwhile working time also. WinRAR is good for all media recordsdata. WinRAR automatically acknowledges and selects essentially the most beneficial compression method. The precise compression algorithm compresses media recordsdata, executables and factor libraries

As I discussed earlier than, the most typical software for dealing with rar files is WinRar WinRar is shareware, however there are quite a few free RAR extractors accessible that may open RAR files. Note that for the reason that rar file format is proprietary, not one of the freeware alternatives can actually create RAR archives. Nevertheless, I still advocate you get a RAR extractor, as a result of you are going to encounter the rar file extension in the end in case you download recordsdata typically.

WinRAR is a data compression software program developed by Eugene Roshal and distributed by Ron Dwight. It was first launched around 1993.1 Though it's a industrial product, there is a free trial. Methods to Set up a Free Suitable DVD Decoder You may simply eliminate Win 7 Anti-Spyware and adware 2011 by clicking So that you wish to obtain Kirby Super Star Ultra Without spending a dime ? Properly there are numerous sites that offer free Dsi video games however they mostly just want your e mail tackle to spam you. So if you wish to Download Kirby Super Star Ultra I counsel you join a Dsi membership website. Home windows 2000 just isn't supported by WinRAR and WinRAR self-extracting Comply with the next step-to-step guide to recover WinZIP/ZIP passwords easily with ZIP Password Restoration 5.zero ( Free Trial ) now. 250 - a hundred and sixty MSP ( FREE )
Hack Designed by Julien Verlaguet, Alok Menghrajani, and others 1 Developer Facebook Appeared in 2014 Typing discipline static , dynamic , weak Influenced by PHP , Java , C# OS Cross-platform Website
However, you'll want to accomplish that with caution so as to don't be panelized by legislation thanks to illegal entry to somebody's privacy upon Facebook account. Really, without acceptable extreme care getting used your wager to hack a Facebook account, you can easily seize yourself in bother in addition to expose your computer to lots of viruses and earthworms just by downloading some unguaranteed and unreliable hacking software program program into your private computer.
This is one of the hottest methods to hack Facebook account it's the one of the best common and favourite technique for Fb hackers. Phishing not only means that you can hack Facebook but additionally can be used to hack any email account. It's a must to only get the trick used to make a phisher, which i feel could be very easy. Phishing is likely one of the easiest strategies to foll somebody and get Facebook account password. I mention the method for instructional objective only.I'll go explaing in particulars on my next article on The way to hack Fb password.

As a website individual we have to implement techniques to shield ourselves from Fb hacks. The very first thing we should absolutely begin doing is to not feel something we hear or maybe see on the internet, never take into account anything at face price! Trusting everybody Pirater mot de passe Facebook on the Internet can result in having your important and personal details stolen. Something you are able to do to safeguard your Fb account is to decide on a sound password. Most safety passwords are simpler than you suppose to crack as a result of folks don't place enough thought into the toughness of their password. Concerning the Writer.
Zynga Poker On line casino Treasured steel & Chips Hack Online poker On line casino Gold & Chips Hack poker chips is often a weblog dedicated to information about Texas maintain em texas holdem games for social networking sites on-line. Visitors can discover information on tips on how to purchase Zynga Poker On line casino Gold & Potato chips Hack Poker On line casino Precious steel & Chips Hack poker chips, tips on how for you to win chips, news about sport coders, articles about strategy Fb Poker On line casino Gold & Poker chips Hack the psychology of online players, Zynga Poker On line casino Gold & Chips Hack different useful data regarding trends in online social gaming.

If you want assist service for Hotmail , it's best in case you can visit official web site for Hotmail tech support. It is without doubt one of the finest sources for tech help because it has considerable data on different subjects that users experience. The directions have comprehensive information on how one can handle issues and stop it from happen once more sooner or later. For any points comparable to Hotmail account configuration or password restoration, one can take help from the web site.

The third and remaining technique to crack a Hotmail password is by brute forcing with a wordlist or dictionary file. This technique would be one of the best because the password will probably be retained and not reset which is not going to set off the account owner's attention whilst you can entry and think about the emails. Aside from that, there are additionally many primary users that makes use of common passwords which will be simply cracked. There are numerous brute forcing tools that may be found on the Web but most of them are both broken (not working) or infected by malware. Now we have found a script written by Adam Joseph that works and is safe to make use of.

Facebook does not actually publicize their business side very much but it is there. You will see that the link on the backside of the article, listed under assets. They allow you to create advertisements that will pop up when individuals are looking their web site Pirater mot de passe Hotmail 2014 to hook up with their acquaintance. The one side impact is that you 'll should pay when people click on your adverts, or when the advert show up, as much as the restrict of your each day finances; however creating a Fb web page for your enterprise is free.

Hotmail has given us few problems, so I'll proceed using them. Open up a brand new Hotmail account for trash email. The final time Toys R Us requested me for my e-mail account I advised her it was “trash” at hotmail dot come. It has worked for years, as soon as a month I will go into that account and delete every thing in it. One can open its own account by visiting on the web site of Hotmail and enjoy the providers of the identical. It's considered as top-of-the-line communication media for the internet users. And since its evolution it has achieved great heights among the competitors. Hotmail is understood for its simplicity and efficiency and it's considered as one of the visited portals within the class of internet service providers. Hotmail Errors on Web page I Can't Load Hotmail

Think about a scenario for a Gmail account. Google has conquered our on-line world. It is the login for our email, adwords, adsense, purchasing account in addition to used as an username for third occasion providers like Paypal, and many others. If for some reason the Gmail account has been compromised then all different accounts are also in peril. This all might happen just because we needed to examine a good friend's e mail forward or a newsletter. The solution is having one thing as semi-login. When logged in using semi-login, we should only have entry to emails that are pre-decided by the person to be shown when he's in full login.

Microsoft Excel 2007 present workplace customers with superior options, which lets you password defend your Excel Workbook or Excel Sheet and no one can modify it until and until you enter the right password to open. Password defending your Excel workbook or sheet can stop others from tampering together with your data.

Actually, you possibly can still have the chance to take away RAR password with a RAR password remover if you happen to forgot the RAR password to entry into There are numerous RAR password removers and RAR Password Unlocker is proved to be a useful instrument for users to recover forgotten RAR password with three efficient options for RAR password recovery. Moreover, it may well speed up the password recovery pace considerably by utilizing superior search algorithm, multiple-core CPUs and NVIDIA-GPU acceleration. Following is a straightforward guide to remove RAR password.

You will need to word that the receiver of your information need to also have WinRAR installed and the entire parts in the same folder. I cannot emphasize this level enough, all of those parts must be in the identical folder, which this is accomplish, the receiver will right-click on part 1 of the file and select "extract right here" , which can give them the video file. In contrast to ZIP, there isn't any have to extract half 2, as a result of it was robotically achieved for you. The receiver can now delete the RAR part files and has the video.

RAR Password Unlocker three.2 is designed to search out the misplaced password for the WinRAR / RAR file for you to extract the recordsdata in the archive easily. This WinRAR / RAR password recovery software helps all variations of WinRAR / RAR archives. It might recover WinRAR / RAR password no matter how lengthy and how complex it's. Enhanced by brute-power attack, brute-drive with mask attack, dictionary assault, it really works successfully and effectively. Furthermore, it is the ever best-to-use program that even a new user can get used to it.

Once you forget RAR password , you may select one of many assault sorts that can assist you take away RAR password The trial model of this RAR password remover will help you remove RAR password inside 3 characters. So you'll be able to evaluate the RAR password remover earlier than you make your decision. Once you neglect RAR password, you'll be able to choose one of WinRar Mot de passe Retirez the assault varieties that will help you remove RAR password. The trial version of this RAR password remover can assist you remove RAR password within three characters. So you possibly can evaluate the RAR password remover before you make your determination. WinRar Password Unlocker is free and it will always be free. obtain winrar password restoration winrar password restoration download winrar password restoration free download winzip password cracker free rar password unlocker
When you may have those packages that give you a message that says "Can't find the chosen program to open the file with" and then it tells you to try and find the selected program on-line or choose a program from an inventory and it's just a ache WinRAR is a straightforward answer to this. When you've gotten this drawback simply go to the containing folder of the program and right click on it and select "Extract here". WinRAR will extract it within the containing folder after which you possibly can double click on the extracted file and you bought your self a solution to your drawback.