Title:
Horacio Moreno ITEC 5321 Spring 2006
Lab Narrative and Reflections,
Windows Vulnerabilities, NetBus, Malicious Code Management and Hoaxes, Network Security Tools
Purpose:
The goal here is to understand what Windows is vulnerable to. It also aids in explaining how to use programs that mitigate the probability a threat will exploit a particular vulnerability (risk).
Tools:
Legion for Windows, DumpSec for Windows, SMBGrind for Windows, SnadBoy’s Revlation for Windows, PWDump for Windows, L0phtCrack for Windows, LSADump2 for Windows, ClearLogs for Windows, Netbus, Zone Alarm, and LanGaurd.
Lab 3A-1 Windows 2000 Vulnerabilities
Lab 3A-4 NetBus
Lab 5A-1 Malicious Code Management and Hoaxes
Lab Manual, Exercise 4A-1, Firewalls
Lab Manual, Exercise 4A-3, File Integrity Monitoring with LanGuard
Procedures:
First we used many tools designated to exploit windows vulnerabilities.
Here we used Legion to locate and attach to a shared windows drive.
Image
Here we extracted remote system information with DumpSec.
Image
Here we broke NetBIOS-SMB passwords and hashes with SMBGrind.
Image
Here we revealed hidden password fields with SnadBoy’s Revelation.
Image
Here we cracked the Windows SAM File with PWDump3 and L0phtCrack
Image
Here we exploited trust with LSADump2.
Image
Here we eradicated windows event logs with ClearLogs.
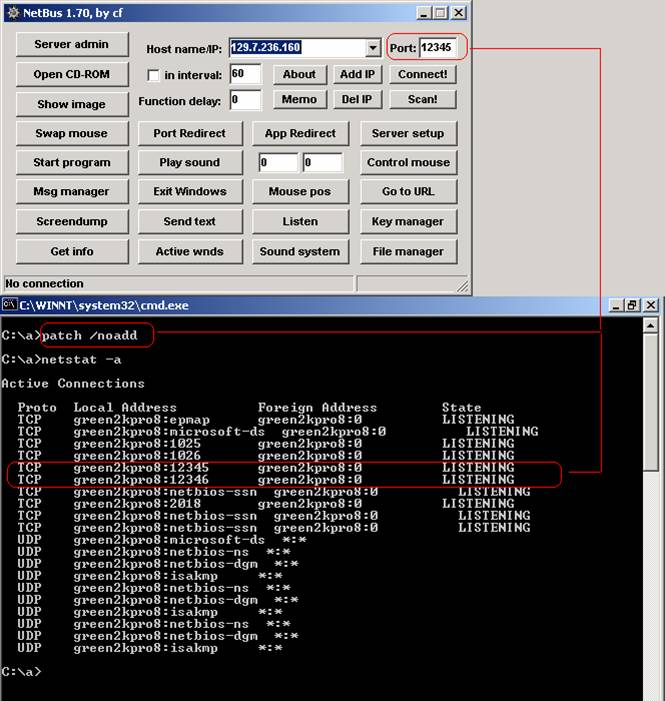
Here we installed the patch (client side) of NetBus on each others computer. Then we ran NetBus (server) to manipulate each others computer.
As you can see the patch opened up TCP port 12345.
We then moved on to read about malicious code and hoax emails.
Next we installed and configured a software based firewall Zone Alarm.
To conclude the lab we did some file integrity monitoring with LanGuard.
Analysis:
While windows vulnerabilities may outwit available defenses, security can be hardened by implementing it in layers.
Time:
About ? hours
Reflection:
I would have never thought you could reveal a hidden password within a form’s password textbox.