Every place in the cyberspace got its own look. Its own feel. Its own charm. Just as the looks of the places change, their properties do as well. Some systems bet on speed. Others are geared at providing maximum security. When intruding a system one should have a careful look at how it is designed.
There are countless fields. Every machine that is connected to cyberspace got its own one. Just describing the looks of each would be pagefilling. Procedure designers account for that and write their stuff in a way that it adapts to different environments. However some characteristics of the location are still important to know.
To ease the navigation within the web a standard template has been done to represent all systems:

What is show is the most basic information about a system (more information can only be obtained by trading for it or by gaining access to the system in question). The knowledge that is easily aquireabe when asking around.
It usually has 5 values:
- Name of the System.
- Operating System: The school the field is based on. It is also the school it is most vulnerable to. Knowledge in that school eases an intrusion. Note that a system can have more then one operating system.
- Defense Rating: The number in the green logo denotes the percentage that a hack will fail against this system.
- Ice Rating: The number in the blue logo denotes the percentage that a failed hack will trigger ICE. Note that it does not show how strong the ICE is or if it is Black ICE!
- I/O Ports (pink icon): The number of backbone connections a system can have to the outside world. A system can only have connection to as many systems as that number denotes.
- Finally there might be a phone icon on the lower right of the system. This icon denotes a modem line that you can call.
Besides the system information also the state of a system is represented in the symbolic notation:

In the above example each star icon represents one hacker. The blue, pink and green one all got access to the system, while the red hacker got root access.
Besides the player icons also two other state icons exist:
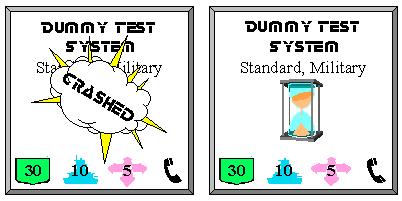
The icon on the left, as the writing suggests, denotes a crashed system, while the right icon is the infamous sand-clock. It indicates that the system is currently blocked due to some heavy activity (a cyber fight usually).
 Locations
Locations

