| Home | Printers | Routers | Tutorials | Firewalls | Security | Health |
Apache systems Zyxell Firewall
1. What is a network firewall?
A firewall is a system or group of systems that enforces an access-control policy between two networks. It may also be defined as a mechanism used to protect a trusted network from an untrusted network. The firewall can be thought of two mechanisms. One to block the traffic, and the other to permit traffic.
The ZyWALL is pre-configured to automatically detect and thwart Denial of Service (DoS) attacks such as Ping of Death, SYN Flood, LAND attack, IP Spoofing, etc. It also uses stateful packet inspection to determine if an inbound connection is allowed through the firewall to the private LAN. The ZyWALLsupports Network Address Translation (NAT), which translates the private local addresses to one or multiple public addresses. This adds a level of security since the clients on the private LAN are invisible to the Internet.
3. What are the basic types of firewalls?
Conceptually, there are three types of firewalls:
Packet Filtering Firewalls generally make their decisions based on the header information in individual packets. These header information include the source, destination addresses and ports of the packets.
Application-level Firewalls generally are hosts running proxy servers, which permit no traffic directly between networks, and which perform logging and auditing of traffic passing through them. A proxy server is an application gateway or circuit-level gateway that runs on top of general operating system such as UNIX or Windows NT. It hides valuable data by requiring users to communicate with secure systems by mean of a proxy. A key drawback of this device is performance.
Stateful Inspection Firewalls restrict access by screening data packets against defined access rules. They make access control decisions based on IP address and protocol. They also 'inspect' the session data to assure the integrity of the connection and to adapt to dynamic protocols. The flexible nature of Stateful Inspection firewalls generally provides the best speed and transparency, however, they may lack the granular application level access control or caching that some proxies support.
4. What kind of firewall is the ZyWALL?
5. Why do you need a firewall when your router has packet filtering and NAT built-in?
With the spectacular growth of the Internet and online access, companies that do business on the Internet face greater security threats. Although packet filter and NAT restrict access to particular computers and networks, however, for the other companies this security may be insufficient, because packets filters typically cannot maintain session state. Thus, for greater security, a firewall is considered.
6. What is Denials of Service (DoS)attack?
Denial of Service (DoS) attacks are aimed at devices and networks with a connection to the Internet. Their goal is not to steal information, but to disable a device or network so users no longer have access to network resources.
There are four types of DoS attacks:
7. What is Ping of Death attack?
Ping of Death uses a 'PING' utility to create an IP packet that exceeds the maximum 65535 bytes of data allowed by the IP specification. The oversize packet is then sent to an unsuspecting system. Systems may crash, hang, or reboot.
Teardrop attack exploits weakness in the reassemble of the IP packet fragments. As data is transmitted through a network, IP packets are often broken up into smaller chunks. Each fragment looks like the original packet except that it contains an offset field. The Teardrop program creates a series of IP fragments with overlapping offset fields. When these fragments are reassembled at the destination, some systems will crash, hang, or reboot.
SYN attack floods a targeted system with a series of SYN packets. Each packet causes the targeted system to issue a SYN-ACK response, While the targeted system waits for the ACK that follows the SYN-ACK, it queues up all outstanding SYN-ACK responses on what is known as a backlog queue. SYN-ACKs are moved off the queue only when an ACK comes back or when an internal timer (which is set a relatively long intervals) terminates the TCP three-way handshake. Once the queue is full , the system will ignore all incoming SYN requests, making the system unavailable for legitimate users.
In a LAN attack, hackers flood SYN packets to the network with a spoofed source IP address of the targeted system. This makes it appear as if the host computer sent the packets to itself, making the system unavailable while the target system tries to respond to itself.
11 What is Brute-force attack?
A Brute-force attack, such as 'Smurf' attack, targets a feature in the IP specification known as directed or subnet broadcasting, to quickly flood the target network with useless data. A Smurf hacker flood a destination IP address of each packet is the broadcast address of the network, the router will broadcast the ICMP echo request packet to all hosts on the network. If there are numerous hosts, this will create a large amount of ICMP echo request packet, the resulting ICMP traffic will not only clog up the 'intermediary' network, but will also congest the network of the spoofed source IP address, known as the 'victim' network. This flood of broadcast traffic consumes all available bandwidth, making communications impossible.
12. What is IP Spoofing attack?
Many DoS attacks also use IP Spoofing as part of their attack. IP Spoofing may be used to break into systems, to hide the hacker's identity, or to magnify the effect of the DoS attack. IP Spoofing is a technique used to gain unauthorized access to computers by tricking a router or firewall into thinking that the communications are coming from within the trusted network. To engage in IP Spoofing, a hacker must modify the packet headers so that it appears that the packets originate from a trusted host and should be allowed through the router or firewall.
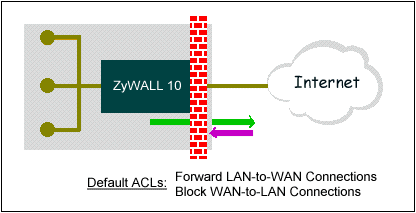
13. What are the default ACL firewall rules in ZyWALL?
There are two default ACLs pre-configured in the ZyWALL, one allows all connections from LAN to WAN and the other blocks all connections from WAN to LAN except of the DHCP packets.

14. Does DMZ behind NAT or not, In ZyWALL 100 ?
Basically DMZ is behind NAT. But there is one exception. If you use Full Feature as NAT type, and there is no NAT mapping for systems on DMZ. Then NAT will not take effect in this case.
15. Can I use both public and private IP addresses on DMZ?
Yes, you can. To achieve this, you have to use IP alias to separate the DMZ interface into 2 logical segments, one for private IP, and the other for public IP.
Then
you have to use Full Feature as NAT type in Menu 4.
Set
NAT mapping for private IP addresses in Menu 15.1.
16. Why traffic redirect/static/policy route be blocked by ZyWALL?
ZyWALL is an ideal secure gateway for all data passing between the Internet and the LAN/DMZ. For some reasons (load balance or backup line), users may want traffic to be re-routed to another Internet access devices while still be protected by ZyWALL. In such case, the network topology is the most important issue. Here is a common example that people mis-deploy the LAN traffic redirect and static route.

The above figure indicates the "triangle route" topology. It works fine if you turn off firewall function on ZyWALL box. However, if you turn on firewall, your connection will be blocked by firewall because of the following reason.
Step 1. Being the default gateway of PC, ZyWALL will receive all "outgoing" traffic from PC.
Step 2. And because of Static route/Traffic Redirect/Policy Routing, ZyWALL forwards the traffic to another gateway (ISDN/Router) which is in the same segment as ZyWALL's LAN.
Step 3. However the return traffic won't go back to ZyWALL, in stead, the "another gateway (ISDN/Router)" will send back the traffic to PC directly. Because the gateway (say, P201) and the PC are in the same segment.
When firewall is turned on, ZyWALL will check the outgoing traffic by ACL and create dynamic sessions to allow return traffic to go back. To achieve Anti-DoS, ZyWALL will send RST packets to the PC and the peer since it never receives the TCP SYN/ACK packet. Thus the connection will always be reset by ZyWALL.Solutions.
(A) Deploying your second gateway in IP alias segment is a better solution. In this way, your connection can be always under control of firewall. And thus there won't be Triangle Route problem.

(B) Deploying your second gateway on WAN side.

(C) To resolve this conflict, we add an option for users to allow/disallow such Triangle Route topology in both CI command and Web configurator . You can issue this command, "sys firewall ignore triangle all on" , to allow firewall bypass triangle route checking. In Web GUI, you can find this option in firewall setup page.
But we would like to notify that if you allow Triangle Route, any traffic will be easily injected into the protected network through the unprotected gateway. In fact, it's a security hole in protected your network.
All contents copyright (c) 2000 ZyXEL Communications Corporation.